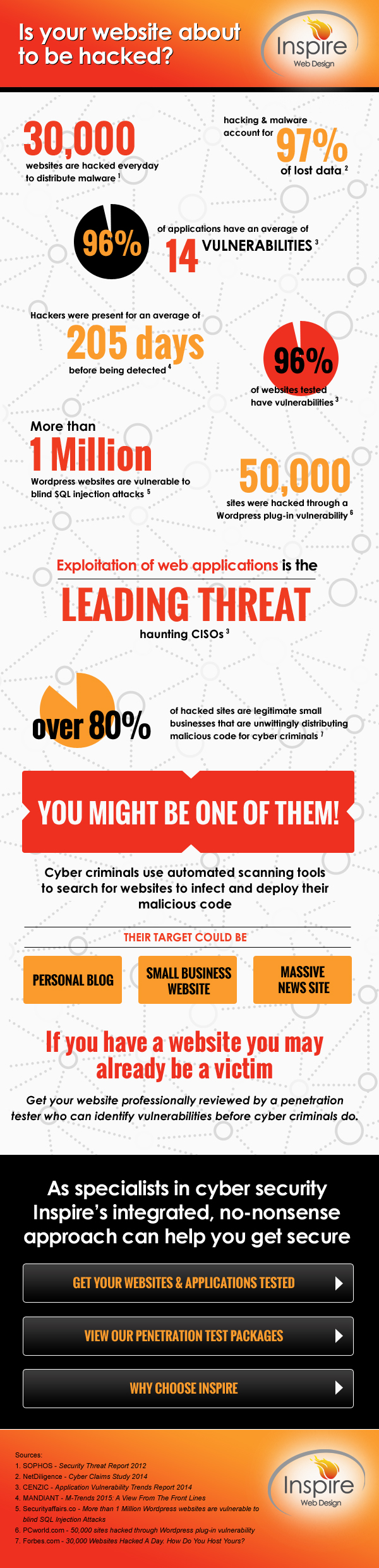
Doom and Gloom: Is your website about to be hacked? |
|
by David Dwyer on 30/07/2015 |
|
What's the implication of getting it wrong? Naturally the prime motivation for our clients is to get back online as quickly as possible, and so they turn to our Developer SOS services to help get them back on track. Our Save our Site service says what it does on the tin, to borrow from a well-known TV ad. We help them regain control of their site and return it to being an asset to their business. We know only too well though that simply fixing the site isn’t enough. There could well be a host of other security vulnerabilities with the site that could have a long-lasting impact on your business. Hackers could, for example, take control of your mail server and use it to send spam email, if that goes undetected for long enough there is a good chance that your domain will be blacklisted. The result? Your recipients email servers reject emails you send. That’s why we perform a Penetration Test because simply fixing the issue simply isn’t enough.
It's worth noting that hackers aren't necessarily hacking for financial gain, for most it is a sport, an opportunity to showcase their ability to gain access to places where they shouldn't be. Some use it as a means of embarrassing an organisation by displaying alternative versions of their logo, or changing the copy on the site. While for others, such as ISIS, the motives are political or ideological in nature. The FBI recently warned that the terror group instigated numerous attacks on sites created on the Wordpress content management system (CMS) platform. Wordpress isn’t the only Open Source CMS’s to be targeted by hackers. In late 2014 the Drupal CMS was aggressively targeted, with as many as 12 million sites being impacted. There is another group of hackers that just want to learn how to hack better. Even developers with little or no experience of coding can accelerate their learning through the ‘dark web’. Here the rookie hacker can download detailed instructions and tools to help them hack better. Regardless of the content on your site, and how worthless you consider it to be, you could find yourself in the unlucky position of simply being in the wrong place, at the wrong time.
Penetration tests explore all vulnerabilities, from Server Side Operating System weaknesses to fundamental TCP/IP flaws such as the notorious Heartbleed bug. At Inspire, we believe passionately in protecting our clients’ sites, web applications and business. Web penetration testing should be part of our clients business continuity process.
The most significant benefit though is that it protects your reputation and your bank balance. Adding penetration testing to your development will cost significantly less than trying to repair an attack after the event.
Are you interested in performing a penetration test on your site? Get in touch with Frazer for a no obligation, informal chat on 01738 700 006 or via our Developer SOS contact us form
David Dwyer is Managing Director of Inspire Web Development. He has years of experience in a range of web and IT roles plus seven years in sales and marketing in a blue-chip FMCG company. David’s academic and professional qualifications include a BA (Hons) in Business Economics (Personnel & Ergonomics) from the University of Paisley, an MSc in Information Technology (Systems) from Heriot-Watt University and PRINCE2 Practitioner-level certification. He is also an active member of the British Computer Society, Entrepreneurial Exchange and Business for Scotland.
Follow Inspire on Twitter @inspireltd and @developersos |
|
CMS, Content Management Systems, Cyber Crime, Cyber Security, Developer SOS, Drupal, Heartbleed Bug, Inspire Web Development, Joomla, Outsourced Web Development, Security, The Evolving Web, The Ghost Vulnerability, Web Consultancy, Web Design, Website Support, Website Vulnerabilities, Wordpress
|